Cryptocurrency Security Guide
May 10, 2019・5 min read
At CoinTracker, the security of your data is foundational to everything we do. We take significant measures to protect your information, and request read-only API keys whenever possible. We don’t store any private keys because security is a top priority for us.

While we do our best to protect users, unfortunately stories of users losing funds to hackers and bugs are far too common. This week 7,000 BTC (~$41 million) was stolen from Binance.
The biggest challenge in securing your crypto is considering the variety of attack vectors and layers of protection that are necessary to truly ensure your funds are safe. There are three primary layers of security to consider when protecting cryptocurrency funds:
- Network — are your private keys cryptographically secure? Is the blockchain secure from a network attack (like a 51% attack)?
- Application — does a third party (e.g. exchange or application) control your coins? How do they store their funds? Do they have an insurance policy? How is your account login secured?
- Real World — are you vulnerable to offline attacks? Is your computer/device secure and encrypted? Is your phone/2FA account safe from attacks? Have you provided recovery instructions to your beneficiaries in the event you die?
Navigating all of these issues can be very challenging, but the good news is there are a growing number of practices and tools designed to help users secure their coins. There are two crucial practices in particular every user should familiarize themselves with: self-custody and cold storage.
Self-custody
“Not your keys, not your bitcoin.” — Andreas Antonopoulos
The most important security measure you can take is to control your own private keys for your cryptocurrency. This means minimizing funds kept on centralized exchanges and applications. While Binance was the most recent exchange to be compromised they are not the first nor will they be the last.
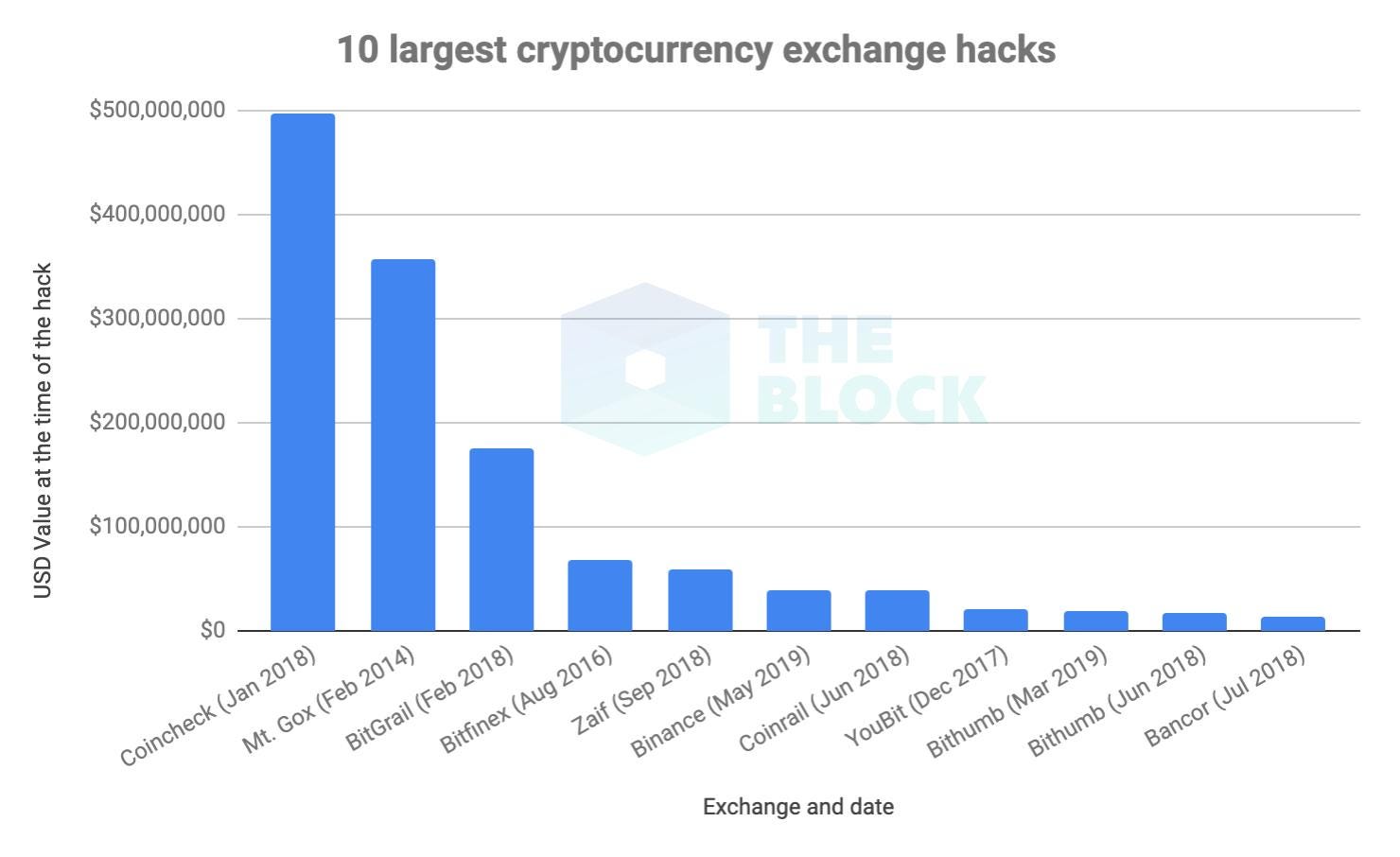
If you do not control your private keys, do not assume your funds are safe — they are only as secure as the company holding onto them and large exchanges and applications like Binance and Coinbase will always be a honeypot for hackers.
CoinTracker can help here by surfacing your exposure to funds held on exchanges so you can always monitor your risk.

Cold Storage
Cryptocurrency can be stored in one of two kinds of wallets: “hot” wallets (connected to the internet) or “cold” storage (offline, disconnected from the internet such as hardware or paper wallets). While funds in hot wallets are generally more easily tradable and thereby more liquid (this is starting to change with decentralized exchanges, relayers, atomic swaps, etc.), cold storage is more secure because a bad actor cannot access the funds remotely.
Rather than keeping most funds in “hot” wallets connected to the internet, you should keep as much cryptocurrency in “cold” storage as possible. Reputable exchanges keep the majority of user funds in cold storage wallets, and this has been effective: exchange hacks have typically involved the theft of “hot wallet” funds but have failed to compromise funds in cold storage.

Most exchanges keep the vast majority of user funds in “cold storage” wallets, and this has been effective: exchange hacks have typically involved the theft of “hot wallet” funds but have failed to compromise funds in cold storage.

The use of cold storage presents its own tradeoffs. While it is easy to deposit funds to a cold storage wallet, it can be a hassle if you need to quickly transfer funds out of a wallet held in cold storage, and each offline wallet system brings its own set of risks.
Hardware Wallets
Hardware wallets are an appealing cold storage solution. In contrast to a software wallet, with a hardware wallet, private keys are stored offline in a protected area of the device and thus cannot be extracted over the internet by a virus or hacker. In contrast to a paper wallet, a hardware wallet is less vulnerable to damage and requires users to press a button on the device to confirm a withdrawal. As a result, an attacker would need physical possession of the device to complete an attack, while once a paper wallet is compromised the attack could occur at any time in the future without possession of the paper wallet.
There are a number of different hardware wallet providers but the most popular are the Ledger and Trezor. Both support Windows, Linux, and OS X devices (they do require a USB connection). They support over a thousand coins but you should check to confirm support (Ledger + Trezor) for your preferred crypto-asset.
Once you have transferred coins to your hardware wallet of choice, you can start tracking them with CoinTracker by adding your xPub key.
At the end of the day there is no silver bullet for cryptocurrency security, but taking these precautions will go a long way toward keeping your funds safe. Beyond protecting your coins, it is also important to maintain an accurate, independent record of your account history so that you have documentation in the event you do lose access to an exchange account or funds.
To make this a bit easier, be sure to head over to CoinTracker and connect your wallets and exchange accounts — you will start receiving notifications of activity across you wallets and exchanges, get insights about the exposure of your funds on exchanges, and more. We are still in the nascent phases of making cryptocurrency useable beyond tech-savvy early adopters and our mission at CoinTracker is to make it safe and easy to use for all.
CoinTracker helps you calculate your crypto taxes by seamlessly connecting to your exchanges and wallets. Questions or comments? Reach out to us @CoinTracker.
Disclaimer: this post is informational only and is not intended as tax advice. For tax advice, please consult a tax professional.